BadZure is a PowerShell script that leverages the Microsoft Graph SDK to orchestrate the setup of Azure Active Directory tenants, populating them with diverse entities while also introducing common security misconfigurations to create vulnerable tenants with multiple attack paths.
Specifically, BadZure automates the process of creating multiple entities such as: users, groups, application registrations, service principals and administrative units. To simulate common security misconfigurations in real environments, it randomly assigns Azure AD roles, Graph permissions and application ownership privileges to randomly picked security principals enabling the creation of unique attack paths. In line with the 'Assume Breach' principle, BadZure provides users with two methods of initial access to the vulnerable tenants it creates thereby simulating account takeover scenarios.
The key advantage of BadZure lies in its ability to rapidly populate and purge existing Azure AD tenants with randomly generated vulnerable configurations and pre-configured initial access facilitating continous and iterative attack simulation (red team) and detection development (blue team) experimentation. It is designed for security practitioners with an interest in exploring and understanding Azure AD security.
BadZure was initialy written to host the Azure AD Battle School: Hands-on Attack and Defense workshop at X33fcon 2023.
An Azure AD tenant populated with BadZure also enables red and blue teams to:
- Experiment with common Azure AD attack vectors and tools (for ideas => AzureAD Attack and Defense Playbook)
- Quickly stand up misconfigured Azure AD lab tenants.
- Obtain attack telemetry to build, test and enhance detection controls
- Execute purple team exercises in a safe setting
- Faciliate hands-on Azure AD security training
- Host dynamic Azure AD Capture the Flag (CTF) events
BadZure facilitates initial access by simulating account takover vectors such as password attacks and token theft. It achieves this through the assignment of a password (randomly generated or user-defined) or by supplying principal JWT access tokens. To support testing strategies such as password spraying, BadZure also automatically generates a 'users.txt' file containing the usernames of the created accounts. The credentials or tokens, made available in the output, enable users to step into the shoes of an attacker who is targeting an Azure AD tenant.
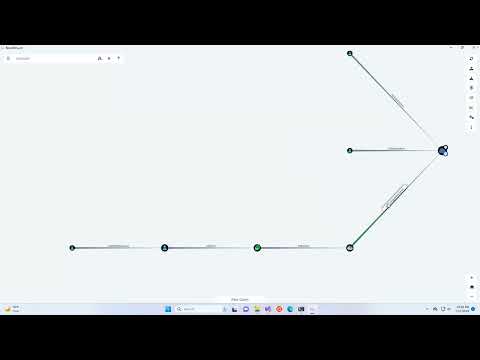
BadZure crafts three privilege escalation attack vectors by simulating service principal abuse scenarios. It achieves this by intentionally introducing misconfigurations caused by Azure AD roles, Graph permissions and application ownerships. A BloodHound-generated graph, showcasing the attack paths BadZure creates, is shown below.
Creating an Azure subscription will also provide you an Azure AD tenant.
Note: Utilizing BadZure within your Azure subscription won't lead to any additional costs as it only requires an Azure AD Free license.
Assign Azure AD roles to users
Install-Module Microsoft.Graph -Scope CurrentUser
git clone https://github.com/mvelazc0/BadZure
cd BadZure
. ./Invoke-BadZure.ps1
# Get Help Menu
Get-Help Invoke-BadZure -Detailed
# Populate a tenant and configure all attack paths with verbose logging
# Note: Authenticate with the new global administrator created in the same directory.
Invoke-BadZure -Build -Verbose
# Populate a tenant and configure a random attack path
Invoke-BadZure -Build $RandomAttackPath
# Populate a tenant, configure all attack pahts and use a custom password for initial access
Invoke-BadZure -Build -Password Summer2023!
# Populate a tenant, configure a random attack path and provide JWT access tokens for initial access
Invoke-BadZure -Build -RandomAttackPath -Token
# Populate a tenant without attack paths
Invoke-BadZure -Build -NoAttackPaths
- Simulate attacks
- Review resulting telemetry
# Destroy all created identities
Invoke-BadZure -Destroy -Verbose
- Mauricio Velazco - @mvelazco
- Cloud Katana by Roberto Rodriguez
- AADInternals by Nestori Syynimaa
- Azure Attack Paths by Fabian Bader
- ROADtools by Dirkjan Mollema
- PurpleCloud by Jason Ostrom
- Azure AD - Attack and Defense Playbook by Sami Lamppu and Thomas Naunheim
- BloodHound/AzureHound by Andy Robbins
- Blog posts, talks and tools by @Haus3c, @kfosaaen, @inversecos and others.
This project is licensed under the Apache 2.0 License - see the LICENSE file for details