Authelia is an open-source authentication and authorization server providing two-factor authentication and single sign-on (SSO) for your applications via a web portal. It acts as a companion for reverse proxies by allowing, denying, or redirecting requests.
Documentation is available at https://www.authelia.com/.
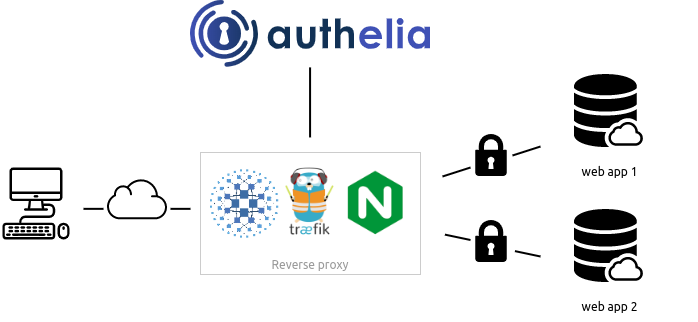
The following is a simple diagram of the architecture:
Authelia can be installed as a standalone service from the AUR, APT, FreeBSD Ports, or using a static binary, .deb package, as a container on Docker or Kubernetes.
Deployment can be orchestrated via the Helm Chart (beta) leveraging ingress controllers and ingress configurations.
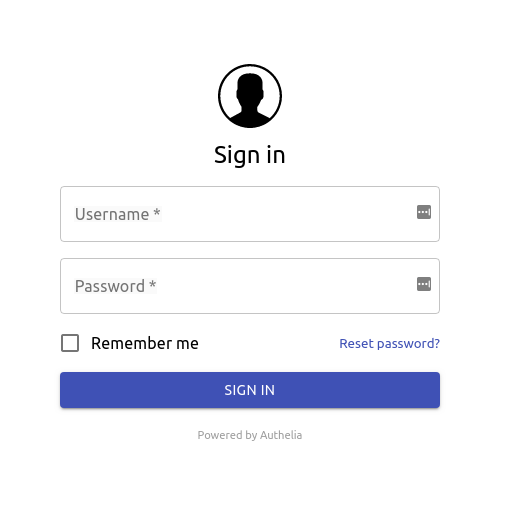
Here is what Authelia's portal looks like:
This is a list of the key features of Authelia:
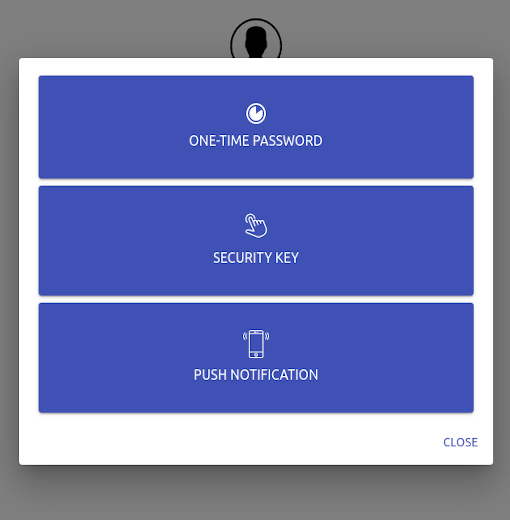
- Several second factor methods:
- Security Keys that support FIDO2 WebAuthn with devices like a YubiKey.
- Time-based One-Time password with compatible authenticator applications.
- Mobile Push Notifications with Duo.
- Password reset with identity verification using email confirmation.
- Access restriction after too many invalid authentication attempts.
- Fine-grained access control using rules which match criteria like subdomain, user, user group membership, request uri, request method, and network.
- Choice between one-factor and two-factor policies per-rule.
- Support of basic authentication for endpoints protected by the one-factor policy.
- Highly available using a remote database and Redis as a highly available KV store.
- Compatible with Traefik out of the box using the ForwardAuth middleware.
- Curated configuration from LinuxServer via their SWAG container as well as a guide.
- Compatible with Caddy using the forward_auth directive.
- Kubernetes Support:
- Compatible with several Kubernetes ingress controllers:
- Beta support for installing via Helm using our Charts.
- Beta support for OAuth 2.0 and OpenID Connect 1.0.
For more details take a look at the Overview.
If you want to know more about the roadmap, follow Roadmap.
Authelia works in combination with nginx, Traefik, Caddy, Skipper, Envoy, or HAProxy.
See the Get Started Guide or one of the curated examples below.
The docker-compose bundles act as a starting point for anyone wanting to see Authelia in action. You will have to
customize them to your needs as they come with self-signed certificates.
The Local compose bundle is intended to test Authelia without worrying about configuration. It's meant to be used for scenarios where the server is not be exposed to the internet. Domains will be defined in the local hosts file and self-signed certificates will be utilised.
The Lite compose bundle is intended for scenarios where the server will be exposed to the internet, domains and DNS will need to be setup accordingly and certificates will be generated through LetsEncrypt. The Lite element refers to minimal external dependencies; File based user storage, SQLite based configuration storage. In this configuration, the service will not scale well.
Now that you have tested Authelia and you want to try it out in your own infrastructure, you can learn how to deploy and use it with Deployment. This guide will show you how to deploy it on bare metal as well as on Kubernetes.
Authelia takes security very seriously. If you discover a vulnerability in Authelia, please see our Security Policy.
For more information about security related matters, please read the documentation.
Several contact options exist for our community, the primary one being Matrix. These are in addition to GitHub issues for creating a new issue.
Community members are invited to join the Matrix Space which includes both the Support Room and the Contributing Room.
- The core team members are identified as administrators in the Space and individual Rooms.
- All channels are linked to Discord.
Community members are invited to join the Discord Server.
- The core team members are identified by the CORE TEAM role in Discord.
- The #support and #contributing channels are linked to Matrix.
You can contact the core team by email via [email protected]. Please note the [email protected] is also available but is strictly reserved for security related matters.
Since Authelia is still under active development, it is subject to breaking changes. It's recommended to pin a version
tag instead of using the latest tag and reading the release notes
before upgrading. This is where you will find information about breaking changes and what you should do to overcome
said changes.
You might wonder why Authelia is open source while it adds a great deal of security and user experience to your infrastructure at zero cost. It is open source because we firmly believe that security should be available for all to benefit in the face of the battlefield which is the Internet, with near zero effort.
Additionally, keeping the code open source is a way to leave it auditable by anyone who is willing to contribute. This way, you can be confident that the product remains secure and does not act maliciously.
It's important to keep in mind Authelia is not directly exposed on the Internet (your reverse proxies are) however, it's still the control plane for your internal security so take care of it!
If you want to contribute to Authelia, please read our contribution guidelines.
Authelia exists thanks to all the people who contribute so don't be shy, come chat with us on either Matrix or Discord and start contributing too.
Thanks goes to these wonderful people (emoji key):
This project follows the all-contributors specification. Contributions of any kind welcome!
Help Wanted: We are actively looking for sponsorship to obtain either a code security audit, penetration testing, or other audits related to improving the security of Authelia.
Any company can become a sponsor by donating or providing any benefit to the project or the team helping improve Authelia.
Thank you to Balto
for hosting our apt repository.
Thank you to JetBrains
for providing us with free licenses to their great tools.
Our pipeline agents which we rely on for productivity are hosted on Azure and our git repositories are hosted on GitHub which are both Microsoft products.
Thank you to all our backers! 🙏 Become a backer and help us
sustain our community. The money we currently receive is dedicated to bootstrap a bug bounty program to give us as many
eyes as we can to detect potential vulnerabilities.
Companies contributing to Authelia via Open Collective will have a special mention below. Become a sponsor.
Authelia is licensed under the Apache 2.0 license. The terms of the license are detailed in LICENSE.