| Acra Engineering Examples | Documentation and tutorials | Installation | Acra feedback |
|---|
Acra — database security suite for sensitive and personal data protection.
Acra provides application-level encryption for data fields, multi-layered access control, database leakage prevention, and intrusion detection capabilities in one suite. Acra was specifically designed for distributed apps (web, server-side and mobile) that store data in one or many databases / datastores.
| Perfect Acra-compatible applications | Typical industries |
|---|---|
| Web and mobile apps that store data in a centralised database or object storage |
|
| IoT apps that collect telemetry and process data in the cloud | |
| High-load data processing apps |
Acra gives you tools for encrypting each sensitive data record (data field, database cell, json) before storing them in the database / file storage. And then decrypting them in a secure compartmented area (on Acra side). Acra allows to encrypt data as early as possible and operate on encrypted data.
Acra's cryptographic design ensures that no secret (password, key, etc.) leaked from the application or database will be sufficient for decryption of the protected data. Acra minimises the leakage scope, detects unauthorised behavior, and prevents the leakage, informing operators of the incident underway.
This is Acra Community Edition, it's free for commercial and non-commercial use, forever.
| encryption on client-side and/or Acra-side – each data field is encrypted using unique encryption keys. | |
| you select which columns to encrypt to balance good security and performance. | |
| two crypto-envelopes: AcraBlocks and AcraStructs. AcraBlocks are fast symmetric containers, use them by default. AcraStructs are asymmetric containers, use them for client-side encryption. |
|
| search through encrypted data without decryption. Designed for exact queries, based on AES-GCM and blind index. | |
| use full or partial masking to remove or mask sensitive data. | |
| substitute sensitive data with a token and match it to original only when needed. | |
| built-in tools for key generation, export, backup, rotation, etc. | |
| through a built-in SQL firewall. | |
| using poison records (honey tokens) to warn about suspicious behaviour. | |
| available for Acra Enterprise users. | |
Acra delivers different layers of defense for different parts and stages of the data lifecycle. This is what defence in depth is – an independent set of security controls aimed at mitigating multiple risks in case of an attacker crossing the outer perimeter.
| all Acra features packed into a database proxy that parses traffic between an app and a database and applies security functions where appropriate. | |
| API server, that exposes most of Acra’s features as HTTP / gRPC API with traffic protection. | |
| optional client-side service for authentication and transport encryption. | |
| available for Acra Enterprise users. | |
| your infrastructure is secure from the start without additional configuring. | |
under the hood | no risk of selecting the wrong key length or algorithm padding. |
| easy to configure and automate. | |
| via binary packages or Docker images. | |
| requires minimal changes in the application code. | |
| throughout all Acra components; compatible with ELK stack, Datadog, Graylog, Prometheus, Grafana, Jaeger. | |
| rollback utilities to decrypt database into plaintext. | |
| numerous web-based and Docker-based example projects available. | |
| run AcraServer in your DigitalOcean cloud. | |
| we can setup and manage Acra for you. |
Acra relies on our cryptographic library Themis, which implements high-level cryptosystems based on the best available open-source implementations of the most reliable ciphers. Acra strictly doesn't contain self-made cryptographic primitives or obscure ciphers.
To deliver its unique guarantees, Acra relies on the combination of well-known ciphers and smart key management scheme. See Cryptography and key management.
| Default crypto-primitive source | OpenSSL |
| Supported crypto-primitive sources ᵉ | BoringSSL, LibreSSL, FIPS-compliant, GOST-compliant, HSM |
| Storage encryption (AcraBlocks) | AES-256-GCM + AES-256-GCM |
| Storage encryption (AcraStructs) | AES-256-GCM + ECDH |
| Transport encryption | TLS v1.2+ or Themis Secure Session |
| KMS integration ᵉ | Amazon KMS, Google Cloud Platform KMS, HashiCorp Vault, Keywhiz, etc |
ᵉ — available in the Enterprise version of Acra only. Drop us an email to get a full list of features and a quote.
Acra consists of several services and utilities. Acra services allow you to construct infinitely sophisticated data flows that are perfectly suited to your exact infrastructure. Depending on your architecture and use case, you might need to deploy only basic services or all of them.
- Security enforcement components: services where "encryption happens". One of them is required: AcraServer, AcraTranslator, AnyProxy, or client-side SDKs.
- Key storage: datastores where Acra keeps encrypted keys: Redis, table in your database, any KV store. One of them is required.
- Master key storage: KMS, Vault. One of them is strongly recommended.
- Additional services and utils: key management utils, data migration scripts, transport security service, policy management tools. Any of them are optional.
Refer to Acra-in-depth / Architecture to learn more about Acra components. Refer to Acra-in-depth / Data flow to see more typical Acra-based dataflows and deployments.
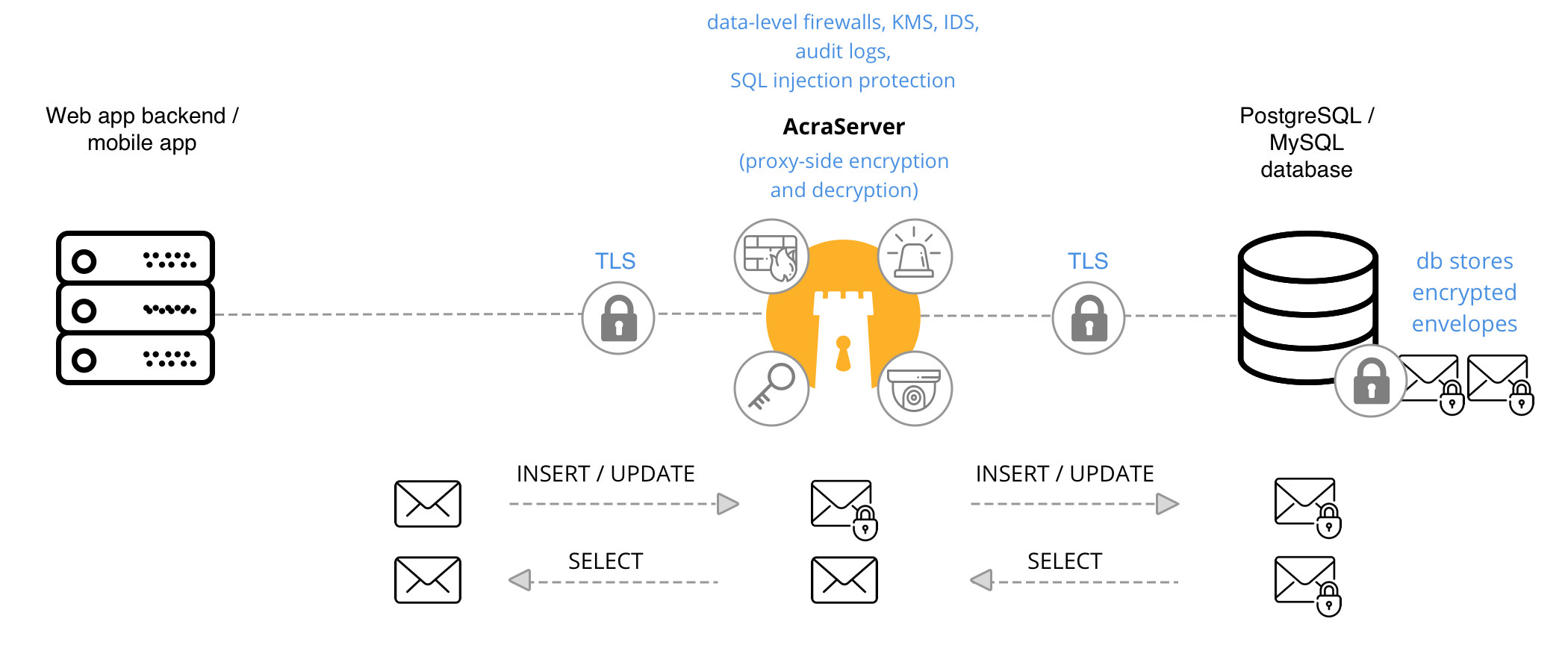
Let's see the simplest dataflow with AcraServer.
AcraServer works as transparent encryption/decryption proxy with SQL databases. The application doesn't know that the data is encrypted before it gets to the database, the database also doesn't know that someone has encrypted the data. That's why we often call this mode a "transparent encryption".
You have a client-side application that talks to the SQL database. You add AcraServer in the middle, working as SQL proxy, and point application to it.
This is what the process of writing and reading the data to/from a database looks like:
- You deploy AcraServer and configure it: connection to the database, TLS certificates, select which fields to encrypt, mask or tokenise, enable SQL request firewall, etc.
- Once AcraServer is deployed, it is ready to accept SQL requests.
- You point the client-side application to the AcraServer instead of the SQL database.
- On receiving SQL queries from the app, AcraServer parses each query and performs security operations: encryption, masking, tokenisation. To know which values to change, AcraServer uses a configuration file where you have described which columns should be encrypted, masked, tokenised.
- After performing the operation, AcraServer passes the modified queries to the database, and the database response – back to the client application. Suppose you select to encrypt the email field: it means that original string is encrypted into cryptographic container and sent to the database as binary data.
- When the client application wants to read the data, it sends a SELECT query to the AcraServer that sends it to the database.
- Upon retrieving the database response, AcraServer tries to decrypt, demask, detokenise specified fields, and returns them to the application.
- Application receives data in plaintext.
Except for data processing operations, AcraServer also analyses SQL queries: blocks the unwanted ones using the built-in configurable SQL firewall, detect SQL injections using poison records, sends logs and metrics, and alerts your Ops team in suspicious cases.
Check out the Guide: Integrating AcraServer into infrastructure to learn more about AcraServer features and how to use them.
Let's see the simplest dataflow with AcraTranslator.
AcraTranslator works as Encryption-as-a-Service using HTTP and gRPC API. The application sends API request to the AcraTranslator with data fields and operations (encryption, decryption, tokenisation, detokenisation, etc). The application is responsible for storing the encrypted data in the database (NoSQL, KV store, SQL, AWS S3 – any) and communicating with AcraTranslator to decrypt it back.
AcraTranslator and AcraServer are fully independent server-side components and can be used together or separately depending on your infrastructure.
You have a client-side application that knows which fields to encrypt, decrypt, tokenise, and where to store them. You add AcraTranslator, and teach the application to perform API calls to use it.
This is what the process of writing and reading the data to/from a database looks like:
- You deploy AcraTranslator in your infrastructure and configure TLS certificates.
- Once AcraTranslator is deployed, it is ready to accept API requests.
- Your application calls AcraTranslator and sends data fields and operations on them (encryption, decryption, tokenisation, detokenisation).
- On receiving API requests, AcraTranslator performs the required operation and sends the result back to the app. Suppose the app sends the "email" field and "encrypt" operation. In that case, the original string is encrypted into cryptographic container and sent back to the app as binary data.
- The application takes encrypted data and stores it in the database/datastore.
- Once the application needs to get plaintext data, it reads encrypted data from the database/datastore, and sends an API request to the AcraTranslator. Suppose the app sends the "email" field and "decrypt" operation. In that case, the original data (binary blob) is decrypted to a string and sent to the app back.
Except for data processing operations, AcraTranslator also analyses API queries: detects intrusions using poison records, sends logs and metrics, and alerts your Ops team in suspicious cases.
Check out the Guide: Integrating AcraTranslator into infrastructure to learn more about AcraServer features and how to use them.
Acra is a suite of components, most of them are "server-side", meaning that you deploy and configure AcraServer, AcraTranslator or AnyProxy, and connect your client-side application to them.
Acra components are compatible with numerous RDBMS, object and KV stores, cloud platforms, external key management systems (KMS), load balancing systems.
| Cloud platforms | DigitalOcean, AWS, GCP, Heroku, any |
| RDBMS | MySQL v5.7+, PosgtreSQL v9.4-v11, MariaDB v10.3; Google Cloud SQL, Amazon RDS |
| Object stores | filesystems, KV databases, Amazon S3, Google Cloud DataStore |
| Load balancing | HAProxy, cloud balancers |
| Server-side platforms | Ubuntu, Debian, CentOS, RHEL; Docker |
| Client-side app language | any :) |
Open source Acra has a limited integration support, more services are available in the Acra Enterprise Edition only.
The server-side Acra components (AcraServer, AcraTranslator, AnyProxy) should run on separate servers/VMs for better isolation and compartmentalization. Key management utils and database helpers are usually run on the same server as AcraServer, AcraTranslator, AnyProxy.
The server-side Acra components run on most Linux distributives (Ubuntu, Debian, CentOS) and as Docker images. Note, the server-side Acra components are not compatible with Windows OS as host OS, consider using Docker.
See Getting started to learn how to install Acra or to try Acra without coding.
Acra works with any client applications. No matter what languages you use to write your apps, you can connect them to AcraServer (via SQL) and AcraTranslator/AnyProxy (via API) to encrypt, decrypt, tokenise and mask the data.
Acra provides a set of client-side SDKs which are useful only in specific use cases:
- AcraWriter – SDK to encrypt data fields into AcraStructs. Use it when encrypting data on the app side is important (for building end-to-end encrypted dataflows or working in hostile environments).
- AcraReader – SDK to decrypt data fields from AcraStructs. Use it when decrypting data on the app side is important (for building end-to-end encrypted dataflows or working in hostile environments).
- SDK for AcraTranslator – SDK that encapsulates AcraTranslator's API for more convenient usage.
These SDKs are available for Ruby, Python, Go, C++, Node.js, iOS (Swift, ObjC), Android (Java, Kotlin), desktop Java and PHP.
See Getting started to learn how to install Acra or to try Acra without coding.
Acra Example Projects illustrate the integration of Acra data protection suite into existing applications: web applications based on Django and Ruby on Rails frameworks, and simple CLI applications. We took well-known apps, detected sensitive data there and added the encryption layer. Protecting the data is completely transparent for the users and requires minimal changes in the infrastructure and application code.
Developers and Ops friendly:
- run a single command to deploy the application, database, Acra's components, logs, and dashboards;
- read the code changes and see how little it takes to integrate encryption into the client application;
- learn how Acra works by reading logs, monitoring metrics in Prometheus, checking tracers in Jaeger and watching Grafana dashboards;
- inspect Docker-compose files, architecture schemes, database tables, and much more.
Requirements: Linux or macOS with installed Docker.
| ⚙️ Run Acra Example Projects ⚙️ |
|---|
The most recent versions of the documentation, tutorials, and demos for Acra are available on the official Cossack Labs Documentation Server.
To gain an initial understanding of Acra, you might want to:
- What is Acra to get an overview of things.
- Acra's security controls to learn more about encryption, masking, tokenisation, SQL firewall, intrusion detections, etc.
- Typical dataflows that shows which Acra components you need and what are the Pros and Cons of each combination.
- Read the notes on Acra's architecture and security design to understand better what you get when you use Acra and what is the threat model that Acra operates in.
You can also check out the speaker slides for the following talks by Cossack Labs engineers:
- "Encryption Without Magic, Risk Management Without Pain" by Anastasiia Voitova.
- "Data encryption for Ruby web applications" by Dmytro Shapovalov.
- "Building SQL firewall(AcraCensor): insights from developers" by Artem Storozhuk.
| ⚙️ Run Acra Example Projects ⚙️ |
|---|
Acra can help you comply with the current privacy regulations, such as:
- General Data Protection Regulation (GDPR)
- HIPAA (Health Insurance Portability and Accountability Act)
- DPA (Data Protection Act)
- CCPA (California Consumer Privacy Act)
Configuring and using Acra in a designated form will cover most of the demands described in articles 25, 32, 33, and 34 of GDPR and the PII data protection demands of HIPAA. Read more about Acra and Regulations.
This is Acra Community Edition, the open source version of Acra, which is 💯 free for commercial and non-commercial usage. Please let us know in the Issues if you stumble upon a bug, see a possible enhancement, or have a comment on security design.
There are also Acra Enterprise Edition available. It provides better performance, redundancy/load balancing, comes pre-configured with crypto-primitives of your choice (FIPS, GOST), has integration with key/secret management tools in your stack, policy management, client-side SDKs, and have plenty of utils and tools for your Ops and SREs to operate Acra conveniently. Talk to us to get full feature lists and a quote.
It takes more than just getting cryptographic code to compile to secure the sensitive data. Acra won't make you “compliant out of the box” with all the modern security regulations, and no other tool will.
We help companies plan their data security strategy by auditing, assessing data flow, and classifying the data, enumerating the risks. We do the hardest, least-attended part of reaching the compliance – turning it from the “cost of doing business” into the “security framework that prevents risks”.
If you’d like to contribute your code or provide any other kind of input to Acra, you’re very welcome. Your starting point for contributing is here.
If you are an Acra user, please leave a short feedback.
Acra Community Edition is licensed as Apache 2 open-source software.
If you want to ask a technical question, feel free to raise an Issue or write to [email protected].
To talk to the business wing of Cossack Labs Limited, drop us an email to [email protected].