This repository contains a target-agnostic Software Framework for the OPTIGA™ Trust X security chip. It is a basis for other application notes. Be aware that this software comes without any security claims and shall be used for evaluation purpose.
The OPTIGA™ Trust X is a security solution based on a secure microntroller. Each device is shipped with a unique elliptic-curve keypair and a corresponding X.509 certificate. OPTIGA™ Trust X enables easy integration into existing PKI infrastructure.
- High-end security controller
- Turnkey solution
- One-way authentication using ECDSA
- Mutual authentication using DTLS client (IETF standard RFC 6347)
- Secure communication using DTLS
- Compliant with the USB Type-C™ Authentication standard
- I2C interface
- Up to 10 KB user memory
- Cryptographic support: ECC256, AES128 (via on-chip DTLS client), SHA-256, TRNG, DRNG
- PG-USON-10-2 package (3 x 3 mm)
- Standard & extended temperature ranges
- Full system integration support
- Common Criteria Certified EAL6+ (high) hardware
- Cryptographic Tool Box based on ECC NIST P256, P384 and SHA256 (sign, verify, key generation, ECDH, session key derivation)
- Lifetime for Industrial Automation and Infrastructure is 20 years and 15 years for other Application Profiles
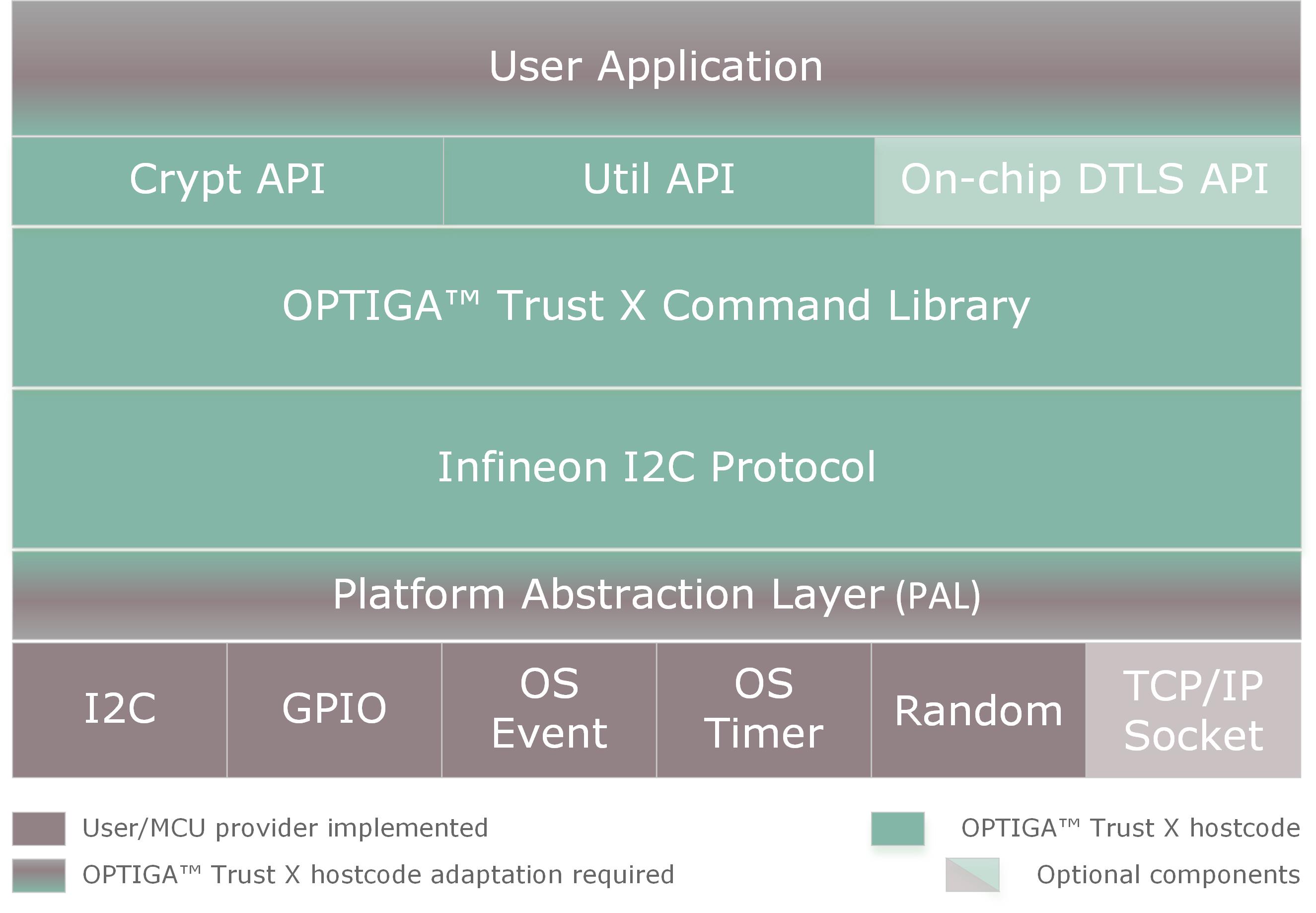
- See Trust X Crypt API and Trust X Util API to know more about optiga_crypt and optiga_util modules
- Information about the OPTIGA™ Trust X Command Library can be found in the Solution Reference Manual v1.35 In the same document you can find explanation of all Object IDs (OIDs) available for users as well as detailed technical explanation for all features and envisioned use cases.
- Infineon I2C Protocol implementation details can be found here
- Platform Abstraction Layer (PAL) overview and Porting Guide are presented in the Wiki
For more information please refer to the Wiki page of this project
- OPTIGA™ Trust X evaluation and demonstration kit
- OPTIGA™ Trust X Shield2Go
- Get started guide
- On-Chip DTLS example
- Off-Chip TLS example (mbedTLS)
- AWS FreeRTOS example
- Secure Firmware Update and Secure Boot
- Arduino library
- Personalize OPTIGA™ Trust
- OpenSSL Engine and Command Line Interface (for RPi3)
- Python package
- I2C Utilities
- OPTIGA Trust X Technical Training
-
User API
-
Hardware-Security: "Einfach (und) Sicher" in German, Slides in English
For high level description and some important excerpts from the documentation please refer to Wiki page
Other downloadable PDF documents can be found below:
- OPTIGA™ Trust X Datasheet v2.6 (PDF)
- OPTIGA™ Solution Reference Manual v1.35 (PDF)
- OPTIGA™ Keys and Certificates v1.2 (PDF)
- Infineon I2C protocol specification v1.65 (PDF)
If you are planning to integrate OPTIGA™ Trust X in your PCB design have a look at the recommendations found here.
Please read CONTRIBUTING.md for details on our code of conduct, and the process for submitting pull requests to us.
This project is licensed under the MIT License - see the LICENSE file for details
Be aware that this software comes without any security claims and shall be used for evaluation purpose.