Using worker: worker-linux-8-1.bb.travis-ci.org:travis-linux-18
git.1
$ git clone --depth=50 git://github.com/jjbohn/omniauth-openid-connect.git jjbohn/omniauth-openid-connect
Cloning into 'jjbohn/omniauth-openid-connect'...
remote: Reusing existing pack: 278, done.
remote: Total 278 (delta 0), reused 0 (delta 0)
Receiving objects: 100% (278/278), 31.21 KiB | 0 bytes/s, done.
Resolving deltas: 100% (106/106), done.
Checking connectivity... done.
$ cd jjbohn/omniauth-openid-connect
git.3
$ git fetch origin +refs/pull/18/merge:
remote: Counting objects: 12, done.
remote: Compressing objects: 100% (10/10), done.
remote: Total 12 (delta 1), reused 0 (delta 0)
Unpacking objects: 100% (12/12), done.
From git://github.com/jjbohn/omniauth-openid-connect
* branch refs/pull/18/merge -> FETCH_HEAD
git.4
$ git checkout -qf FETCH_HEAD
rvm.1
$ rvm use 2.0.0 --install --binary --fuzzy
Using /home/travis/.rvm/gems/ruby-2.0.0-p451
$ export BUNDLE_GEMFILE=$PWD/Gemfile
$ ruby --version
ruby 2.0.0p451 (2014-02-24 revision 45167) [x86_64-linux]
$ rvm --version
rvm 1.25.25 (latest-minor) by Wayne E. Seguin <[email protected]>, Michal Papis <[email protected]> [https://rvm.io/]
$ gem --version
2.2.2
$ bundle --version
Bundler version 1.6.2
install
$ bundle install
Fetching gem metadata from https://rubygems.org/.........
Fetching additional metadata from https://rubygems.org/..
Resolving dependencies...
Installing rake 10.3.2
Installing i18n 0.6.9
Installing json 1.8.1
Installing minitest 5.3.5
Installing thread_safe 0.3.4
Installing tzinfo 1.2.1
Installing activesupport 4.1.1
Installing builder 3.2.2
Installing activemodel 4.1.1
Installing addressable 2.3.6
Installing attr_required 1.0.0
Installing bindata 2.1.0
Using bundler 1.6.2
Installing timers 1.1.0
Installing celluloid 0.15.2
Installing coderay 1.1.0
Installing multi_json 1.10.1
Installing mime-types 2.3
Installing rest-client 1.6.7
Installing docile 1.1.5
Installing simplecov-html 0.8.0
Installing simplecov 0.8.2
Installing tins 1.3.0
Installing term-ansicolor 1.3.0
Installing thor 0.19.1
Installing coveralls 0.7.0
Installing faker 1.3.0
Installing ffi 1.9.3
Installing formatador 0.2.5
Installing rb-fsevent 0.9.4
Installing rb-inotify 0.9.5
Installing listen 2.7.9
Installing lumberjack 1.0.7
Installing method_source 0.8.2
Installing slop 3.5.0
Installing pry 0.10.0
Installing guard 2.6.1
Installing guard-bundler 2.0.0
Installing guard-minitest 2.3.1
Installing hashie 2.1.2
Installing httpclient 2.4.0
Installing securecompare 1.0.0
Installing url_safe_base64 0.2.2
Installing json-jwt 0.6.1
Installing mail 2.6.1
Installing metaclass 0.0.4
Installing mocha 1.1.0
Installing rack 1.5.2
Installing omniauth 1.2.1
Installing rack-oauth2 1.0.8
Installing swd 0.2.1
Installing validate_email 0.1.6
Installing validate_url 0.2.2
Installing webfinger 1.0.0
Installing openid_connect 0.7.3
Using omniauth-openid-connect 0.1.0 from source at .
Your bundle is complete!
Use `bundle show [gemname]` to see where a bundled gem is installed.
$ bundle exec rake
/home/travis/.rvm/rubies/ruby-2.0.0-p451/bin/ruby -I"lib:lib/omniauth-openid-connect" -I"/home/travis/.rvm/gems/ruby-2.0.0-p451/gems/rake-10.3.2/lib" "/home/travis/.rvm/gems/ruby-2.0.0-p451/gems/rake-10.3.2/lib/rake/rake_test_loader.rb" "test/lib/omniauth/openid_connect/version_test.rb" "test/lib/omniauth/strategies/openid_connect_test.rb"
[Coveralls] Set up the SimpleCov formatter.
[Coveralls] Using SimpleCov's default settings.
[Coveralls] Submitting with config:
{
"environment": {
"pwd": "/home/travis/build/jjbohn/omniauth-openid-connect",
"rails_root": null,
"simplecov_root": "/home/travis/build/jjbohn/omniauth-openid-connect",
"gem_version": "0.7.0",
"travis_job_id": "28347137",
"travis_pull_request": "18"
},
"git": {
"head": {
"id": "a7a9f5bf31c744a50c306f19c1babe32ec4dbac2",
"author_name": "Nathan West",
"author_email": "[email protected]",
"committer_name": "Nathan West",
"committer_email": "[email protected]",
"message": "Merge 90707cdb544cf76837bbf15d395cc02c415f73f3 into 88ba03399bb2129e901b8fa6257230934d2e7bb8"
},
"branch": "(detached from FETCH_HEAD)",
"remotes": [
{
"name": "origin",
"url": "git://github.com/jjbohn/omniauth-openid-connect.git"
}
]
},
"service_job_id": "28347137",
"service_name": "travis-ci"
}
[Coveralls] Submitting to https://coveralls.io/api/v1
[Coveralls] Job #62.2
[Coveralls] https://coveralls.io/jobs/2117515
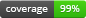
Coverage is at 12.5%.
Coverage report sent to Coveralls.
/home/travis/.rvm/gems/ruby-2.0.0-p451/gems/activesupport-4.1.1/lib/active_support/number_helper.rb:3:in `<module:NumberHelper>': uninitialized constant ActiveSupport::Autoload (NameError)
from /home/travis/.rvm/gems/ruby-2.0.0-p451/gems/activesupport-4.1.1/lib/active_support/number_helper.rb:2:in `<module:ActiveSupport>'
from /home/travis/.rvm/gems/ruby-2.0.0-p451/gems/activesupport-4.1.1/lib/active_support/number_helper.rb:1:in `<top (required)>'
from /home/travis/.rvm/gems/ruby-2.0.0-p451/gems/activesupport-4.1.1/lib/active_support/core_ext/numeric/conversions.rb:2:in `require'
from /home/travis/.rvm/gems/ruby-2.0.0-p451/gems/activesupport-4.1.1/lib/active_support/core_ext/numeric/conversions.rb:2:in `<top (required)>'
from /home/travis/.rvm/gems/ruby-2.0.0-p451/gems/activesupport-4.1.1/lib/active_support/core_ext/numeric.rb:3:in `require'
from /home/travis/.rvm/gems/ruby-2.0.0-p451/gems/activesupport-4.1.1/lib/active_support/core_ext/numeric.rb:3:in `<top (required)>'
from /home/travis/.rvm/gems/ruby-2.0.0-p451/gems/activesupport-4.1.1/lib/active_support/core_ext.rb:2:in `require'
from /home/travis/.rvm/gems/ruby-2.0.0-p451/gems/activesupport-4.1.1/lib/active_support/core_ext.rb:2:in `block in <top (required)>'
from /home/travis/.rvm/gems/ruby-2.0.0-p451/gems/activesupport-4.1.1/lib/active_support/core_ext.rb:1:in `each'
from /home/travis/.rvm/gems/ruby-2.0.0-p451/gems/activesupport-4.1.1/lib/active_support/core_ext.rb:1:in `<top (required)>'
from /home/travis/.rvm/gems/ruby-2.0.0-p451/gems/swd-0.2.1/lib/swd.rb:4:in `require'
from /home/travis/.rvm/gems/ruby-2.0.0-p451/gems/swd-0.2.1/lib/swd.rb:4:in `<top (required)>'
from /home/travis/.rvm/gems/ruby-2.0.0-p451/gems/openid_connect-0.7.3/lib/openid_connect.rb:3:in `require'
from /home/travis/.rvm/gems/ruby-2.0.0-p451/gems/openid_connect-0.7.3/lib/openid_connect.rb:3:in `<top (required)>'
from /home/travis/build/jjbohn/omniauth-openid-connect/lib/omniauth/strategies/openid_connect.rb:4:in `require'
from /home/travis/build/jjbohn/omniauth-openid-connect/lib/omniauth/strategies/openid_connect.rb:4:in `<top (required)>'
from /home/travis/build/jjbohn/omniauth-openid-connect/lib/omniauth/openid_connect.rb:2:in `require'
from /home/travis/build/jjbohn/omniauth-openid-connect/lib/omniauth/openid_connect.rb:2:in `<top (required)>'
from /home/travis/build/jjbohn/omniauth-openid-connect/lib/omniauth-openid-connect.rb:1:in `require'
from /home/travis/build/jjbohn/omniauth-openid-connect/lib/omniauth-openid-connect.rb:1:in `<top (required)>'
from /home/travis/build/jjbohn/omniauth-openid-connect/test/test_helper.rb:11:in `require_relative'
from /home/travis/build/jjbohn/omniauth-openid-connect/test/test_helper.rb:11:in `<top (required)>'
from /home/travis/build/jjbohn/omniauth-openid-connect/test/lib/omniauth/openid_connect/version_test.rb:1:in `require_relative'
from /home/travis/build/jjbohn/omniauth-openid-connect/test/lib/omniauth/openid_connect/version_test.rb:1:in `<top (required)>'
from /home/travis/.rvm/gems/ruby-2.0.0-p451/gems/rake-10.3.2/lib/rake/rake_test_loader.rb:15:in `require'
from /home/travis/.rvm/gems/ruby-2.0.0-p451/gems/rake-10.3.2/lib/rake/rake_test_loader.rb:15:in `block in <main>'
from /home/travis/.rvm/gems/ruby-2.0.0-p451/gems/rake-10.3.2/lib/rake/rake_test_loader.rb:4:in `select'
from /home/travis/.rvm/gems/ruby-2.0.0-p451/gems/rake-10.3.2/lib/rake/rake_test_loader.rb:4:in `<main>'
rake aborted!
Command failed with status (1): [ruby -I"lib:lib/omniauth-openid-connect" -I"/home/travis/.rvm/gems/ruby-2.0.0-p451/gems/rake-10.3.2/lib" "/home/travis/.rvm/gems/ruby-2.0.0-p451/gems/rake-10.3.2/lib/rake/rake_test_loader.rb" "test/lib/omniauth/openid_connect/version_test.rb" "test/lib/omniauth/strategies/openid_connect_test.rb" ]
Tasks: TOP => default => test
(See full trace by running task with --trace)
The command "bundle exec rake" exited with 1.
Done. Your build exited with 1.