AttackVector Linux: the dragon has tails
AttackVector Linux is a new distribution for anonymized security testing.
It is based on custom Kali with ideas gleaned from Tails (both Debian based), with tools not found in either.
Yin and Yang
AttackVector Linux (A.V.L.) is a Kali live-build "recipe", which can be thought of as add-ons for Kali live-build.
The biggest add-on is Tor installed by default. It is taken from Tails' design.
Kali vs. Tails
While Kali requires a modified kernel for network drivers to use injection and so forth,
TAILS is designed from the bottom up for encryption, and anonymity. Nmap can't UDP via Tor.
The intention of AttackVector Linux is to provide the capability to anonymize attacks
while warning the user when he or she takes actions that may compromise anonymity.
The two projects have different design philosophies that can directly conflict with one another.
In spite of this, the goal of AttackVector Linux is to integrate them into one complimentary OS.
- apt/iceweasel/wget all run through tor (using polipo)
- Iceweasel includes cookie monster, HTTPSeverywhere, TORbutton, and other great extensions
- Incredible password recovery tools: hashkill OCLHashcat, many more!
- Great Ruby tools like Ronin
- Every penetration testing security tool from Kali. (Yes, really.)
- Additional tools for pen-testing, password cracking, and more
- Dedicated install with FDE and wordlists galore.
- Other tools like FakeAP, sdmem
- mirror BitBucket
- mirror Act4Security.com
- MD5 (attack_vector_alpha_0.1.1b.iso) = 99243d5f4132116e2e9606d6b0c98e6f
Q: Why are you doing this/whom are you doing this for?
A: My design goals were inspired by security professionals who have little time and/or money to put towards finding new tools/frameworks/configurations that would benefit them. That isn't to say this is the only group of people who will find this distro beneficial, but it is the group that I was hoping would find use in the extended tools/toolsets/configurations.
Q: What's different about this distro, as opposed to Kali?
A: One of the design goals is anonymity, which security professionals require on various job sites, especially for black-box testing. To accomplish this I took much of the TOR/TSOCKS configuration from TAILS and put it in the Kali build, including starting Vidalia with the GNOME3 window manager. I added many things at the behest of friends, including Ronin, FakeAP, and more. I also added a bunch of packages from the regular old Debian repos that I like to see. For a full list (more of less) of changes is listed below
Q: Can Tor be turned off?
A: Yes, to disable Tor globally simple exit Vidalia, then run the command "/etc/init.d/polipo stop", and finally comment out the config in "/etc/apt/apt.conf.d/0000runtime-proxy" and "/etc/wgetrc". FYI, TOR does not affect anything that is not intentionally proxied through Polipo, meaning that it will not interfere with NMAP, etc.
Q: Is this only GNOME 3, or can I switch to MATE/KDE/alternate?
Kaneda: Right now I'm building for GNOME 3 specifically, but I will come out with a KDE version due to popular demand. Feel free to give your input regarding alternate window managers and I'll see what I can do.
Thom: I like compiz, tiling window managers, and buuf icon theme.
Here's a brainstorm:
razor-qt
compiz
qtile
openbox
fluxbox
ion
I also love the Buuf icon theme:
buuf
Q: One of your design goals is a Windows XP theme? (camouflage)
Kaneda: This is one that's up for debate, but given Thom's insistence that we include it I will get around to it at some point in the near future.
Thom: Here's the link from Tails' design: Windows Camouflage, also: phillips321 did it on BT5.
Q: Aren't kiddies going to use this tool to... ChaOS?!
A: Probably. I'm not a lawyer. Here is an official-ish blurb: Customarily, I (@KenSoona) am not responsible for any malicious use of this tool, and I hope that releasing it and its source code engenders better information security for the community at large.
Install prerequisites for Kali build. This can be done in Debian Squeeze, but we recommend starting from a Kali install:
#!/bin/sh
apt-get install git live-build cdebootstrap kali-archive-keyring
cd /tmp
git clone git clone https://[email protected]/attackvector/attackvector-linux.git
apt-get remove libdebian-installer4 # /* We reinstall libdebian-installer4 */
apt-get install libdebian-installer4 # /* due to a weird bug */
cd attackvector-linux/live-build-config
#!/bin/sh
lb clean --purge
dpkg --add-architecture amd64
apt-get update
lb config --architecture amd64 --mirror-binary http://http.kali.org/kali --mirror-binary-security http://security.kali.org/kali-security --apt-options "--force-yes --yes"
lb build
Please submit all requests for bugfixes and features for our next release cycle to JIRA.
We release under an "early, often" philosophy.
- Research labs targeting malware servers such as command and control servers.
- Legitimate penetration testing consulting companies needing to do black-box testing.
hacktivistsworking within oppressive governmental regiemes.- Academics and students working on experimental projects.
- Intelligence agencies seeking plausible deniability.
When I was asking my mentor, a computer security professor, about the ethically grey implications of the project, she replied, "You can always just call it an academic exercise."
Further Q&A (/r/netsec)
Q: How is this different from BackBox?
- 1.) You're right, on the surface, no difference, all this FOSS was available elsewhere (different packages and repositories). However, I'd argue:
- 2.) No one had stiched the pieces together in this particular way. I'd argue that Tails features and design goals like these are noble ones for a Kali fork.
- 3.) Kali's live-build is designed for uses like this. Think of it as a post-install script that runs as you generate the ISO instead, so it's sorta like a pre-install? IDK
via ex-developer @kanedasan:
-
- Tor is not configured "globally". It does not break UDP scans. It is set up such that things like wget and Iceweasel use it out of the box but can easily be switched off (in the case of Iceweasel, just hit the TOR button!)
-
- The additional tools you will find are not ones that many people know about, hence why they were not included in Kali to begin with. Further, I have received permission to distribute any and all of this software (if it did not come with a clear, legal license)
-
- You can go and look at the build scripts: this is how the ISOs are built, feel free to build it yourself and compare the resultant contents
-
- As stated in the FAQ, my design goals are to reach pen-testers and security professionals who do not have the time, money, and/or patience to build such a thing, and use them to get feedback regarding further innovations to this product. The immediate intent is not to aid "hacktivists working within oppressive governmental regiemes," but if it does in fact help them, then that's OK too
-
- This is in ALPHA STAGE: for any and all requests please see our JIRA
<muts> so basically, your project can be represented as a "live-build" recipe.
<`butane> AttackVector merges the tools of Kali and the anonymity of Tails into the scariest Linux security distribution on the internet
- libservice-wrapper-java
- libservice-wrapper-jni
- service-wrapper
- libssl-dev
- libjson0-dev
- amd-opencl-dev
- nvidia-opencl-dev
- adduser
- armitage
- binutils
- bsdutils
- chkconfig
- coreutils
- curl
- diffutils
- dnsutils
- dsniff
- findutils
- florence
- fuse-utils
- gnupg
- gnupg-agent
- gnupg-curl
- gnutls-bin
- gzip
- haveged
- i2p
- i2p-router
- ipheth-utils
- iproute
- iptstate
- iputils-ping
- iputils-tracepath
- john
- john-data
- keepassx
- laptop-mode-tools
- libsqlite3-dev
- libsqlite3-ruby1.9.1
- liferea
- liferea-data
- lockfile-progs
- lua5.1
- lzma
- metasploit
- moreutils
- mtools
- ncurses-base
- ncurses-bin
- net-tools
- netcat-traditional
- nmap
- openssl
- pidgin
- pidgin-data
- pidgin-otr
- polipo
- poppler-utils
- pwgen
- rfkill
- ruby1.9.1
- ruby1.9.1-dev
- rubygems
- seahorse
- seahorse-nautilus
- secure-delete
- sqlite3
- sshfs
- ssss
- thc-hydra
- tor
- tor-arm
- tor-geoipdb
- torsocks
- tsocks
- unar
- unzip
- vim-nox
- vim-runtime
- vim-tiny
- wget
- whois
- xul-ext-adblock-plus
- xul-ext-cookie-monster
- xul-ext-foxyproxy-standard
- xul-ext-https-everywhere
- xul-ext-noscript
- xul-ext-torbutton
- hashkill
- fakeap
- quicksnap
- gem install ronin
- gem install ronin-asm
- gem install ronin-dorks
- gem install ronin-exploits
- gem install ronin-gen
- gem install ronin-grid
- gem install ronin-php
- gem install ronin-scanners
- gem install ronin-sql
- gem install ronin-support
- gem install ronin-web
- polipo -> tor
- wget -> polipo
- apt -> polipo
- sdmem (wipes memory at shutdown/reboot)
- Live Build Manual
- TAILS git branches
- How to build TAILS
- How to customize TAILS
- Rebuilding a Kali Package
- Rebuilding the Kali Kernel
- Live Build a Custom Kali ISO
- How to customize Debian live
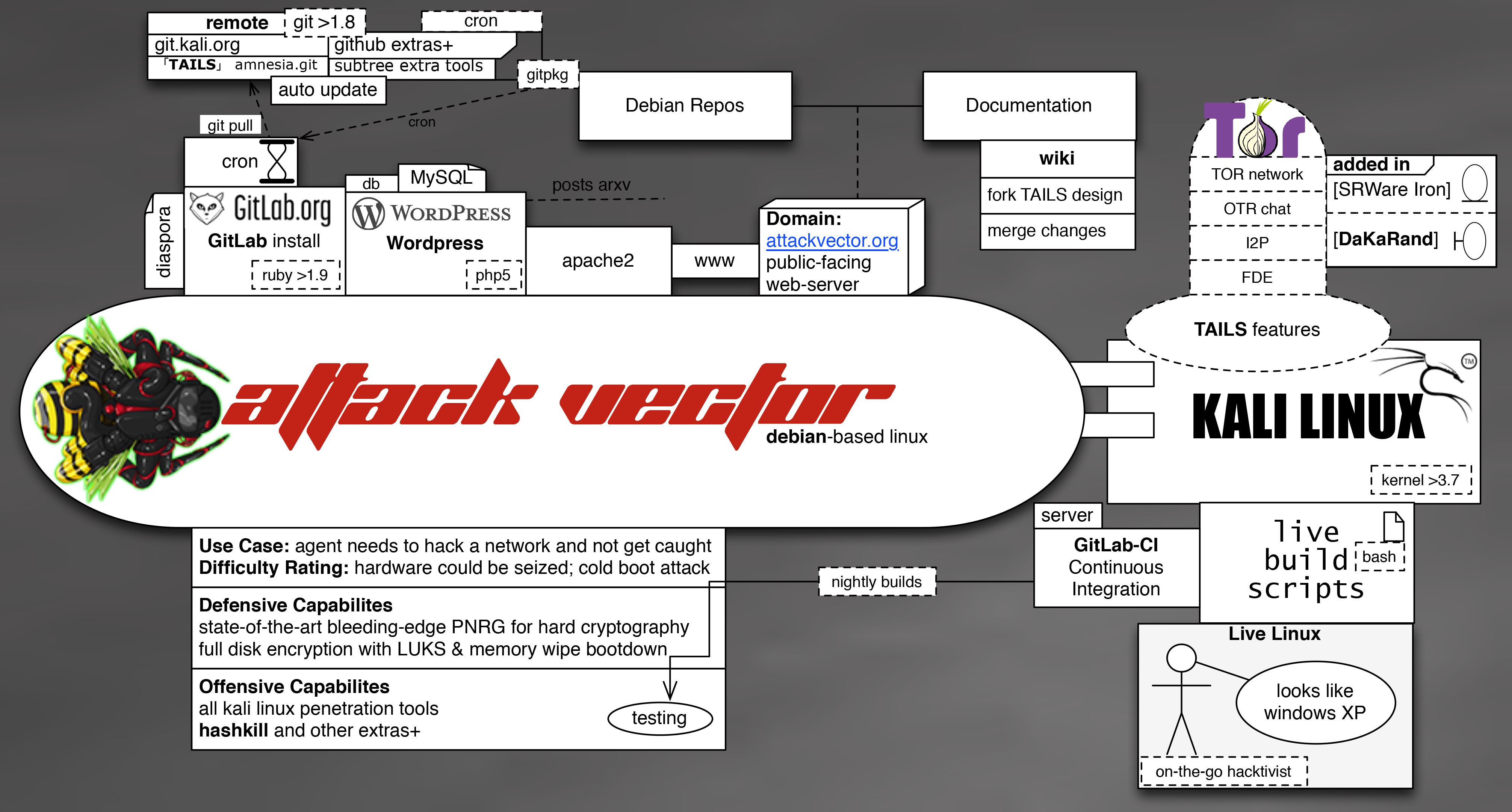
Eventually this Kali derivative should meet the TAILS design specifications.
- Kali git repositories
- TAILS git repository
- Configure build system to generate & test ISOs
- Help port TAILS to Wheezy
- Evaluate features of each distro & unify them into a single kernel
- Provide two layers of functionality: desktop install and live
- Evaluate features of each distro & unify them into a single kernel
- Add warning messages for anonymity risks
- Full Disk Encryption (FDE) w/ LUKS
- on flash storage jump drive for Live Linux
- on dedicated install with wordlists galore
- Host on AttackVector.org
- Provide documentation
- HTTPS Everywhere
- Debian repositories
- Continue to integrate high quality tools
- Clone the Kali repos so that AttackVector can stand-alone
- Change live build to run off this new mirror
- Debian repositories
- Add more tools!
Text under Creative Commons Attribution-NonCommercial-ShareAlike 3.0 Unported License. Code under GNU Public License.