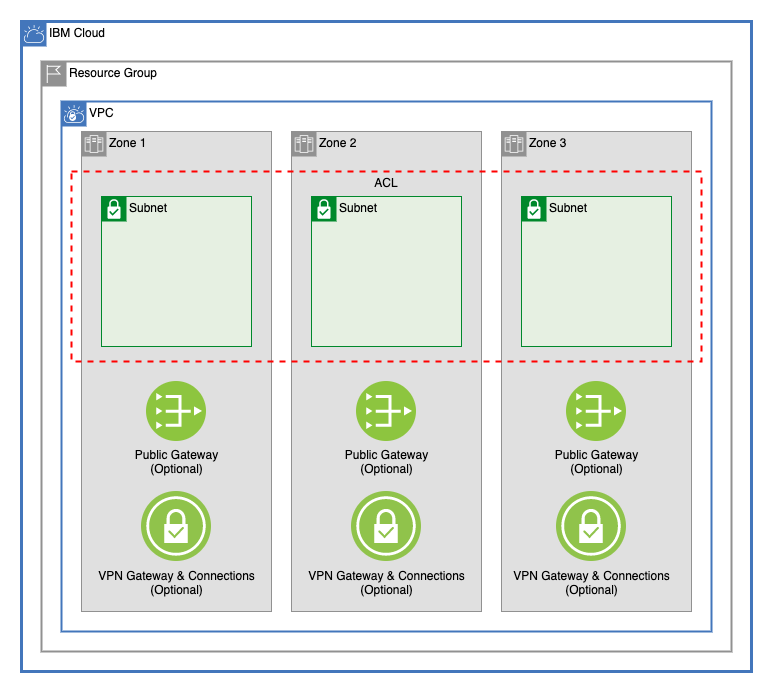
This module creates the following IBM Cloud® Virtual Private Cloud (VPC) network components:
- VPC: Creates a VPC in a resource group and supports classic access. The VPC and components are specified in the main.tf file.
- Public gateways: Optionally create public gateways in the VPC in each of the three zones of the VPC's region.
- Subnets: Create one to three zones in the subnet.tf file.
- Network ACLs: Create network ACLs with multiple rules. By default, VPC network ACLs can have no more than 25 rules.
- VPN gateways: Create VPN gateways on your subnets by using the
vpn_gatewaysvariable. For more information about VPN gateways on VPC, see About site-to-site VPN gateways in the IBM Cloud docs. - VPN gateway connections: Add connections to a VPN gateway.
- Hub and spoke DNS-sharing model: Optionally create a hub or spoke VPC, with associated custom resolver and DNS resolution binding, as well as a service-to-service authorization policy which supports the hub and spoke VPCs to be in separate accounts. See About DNS sharing for VPE gateways in the IBM Cloud docs for details.
In addition to this root module, this repository provides two submodules that call the root module with presets and defaults that are aligned with the general Framework for Financial Services management and workload VPC topologies. See the modules for details.
module vpc {
source = "terraform-ibm-modules/landing-zone-vpc/ibm"
version = "X.X.X" # Replace "X.X.X" with a release version to lock into a specific release
resource_group_id = var.resource_group_id
region = var.region
prefix = var.prefix
tags = var.tags
vpc_name = var.vpc_name
classic_access = var.classic_access
network_acls = var.network_acls
use_public_gateways = var.use_public_gateways
subnets = var.subnets
vpn_gateways = var.vpn_gateways
}The module automatically generates names for the all provisioned VPC resources using the var.prefix input variable. You can selectively override this behavior by giving explicit names through the following input variables: name (for VPC name), dns_binding_name, dns_instance_name, dns_custom_resolver_name, routing_table_name, public_gateway_name, and vpc_flow_logs_name.
You can create a maximum of three zones in the subnet.tf file. The zones are defined as lists in the file, and then are converted to objects before the resources are provisioned. The conversion ensures that the addition or deletion of subnets affects only the added or deleted subnets, as shown in the following example.
module.subnets.ibm_is_subnet.subnet["gcat-multizone-subnet-a"]
module.subnets.ibm_is_subnet.subnet["gcat-multizone-subnet-b"]
module.subnets.ibm_is_subnet.subnet["gcat-multizone-subnet-c"]
module.subnets.ibm_is_vpc_address_prefix.subnet_prefix["gcat-multizone-subnet-a"]
module.subnets.ibm_is_vpc_address_prefix.subnet_prefix["gcat-multizone-subnet-b"]
module.subnets.ibm_is_vpc_address_prefix.subnet_prefix["gcat-multizone-subnet-c"]You need the following permissions to run this module.
- IAM services
- VPC Infrastructure services
Editorplatform access
- No service access
- Resource Group <your resource group>
Viewerresource group access
- VPC Infrastructure services
To attach access management tags to resources in this module, you need the following permissions.
- IAM Services
- Tagging service
Administratorplatform access
- Tagging service
| Name | Version |
|---|---|
| terraform | >= 1.3.0 |
| ibm | >= 1.59.0, < 2.0.0 |
| time | >= 0.9.1, < 1.0.0 |
| Name | Source | Version |
|---|---|---|
| dynamic_values | ./dynamic_values | n/a |
| unit_tests | ./dynamic_values | n/a |
| Name | Description | Type | Default | Required |
|---|---|---|---|---|
| access_tags | A list of access tags to apply to the VPC resources created by the module. For more information, see https://cloud.ibm.com/docs/account?topic=account-access-tags-tutorial. | list(string) |
[] |
no |
| address_prefixes | OPTIONAL - IP range that will be defined for the VPC for a certain location. Use only with manual address prefixes | object({ |
{ |
no |
| classic_access | OPTIONAL - Classic Access to the VPC | bool |
false |
no |
| clean_default_sg_acl | Remove all rules from the default VPC security group and VPC ACL (less permissive) | bool |
false |
no |
| create_authorization_policy_vpc_to_cos | Create authorisation policy for VPC to access COS. Set as false if authorization policy exists already | bool |
false |
no |
| create_subnets | Indicates whether user wants to use existing subnets or create new. Set it to true to create new subnets. | bool |
true |
no |
| create_vpc | Indicates whether user wants to use an existing vpc or create a new one. Set it to true to create a new vpc | bool |
true |
no |
| default_network_acl_name | OPTIONAL - Name of the Default ACL. If null, a name will be automatically generated | string |
null |
no |
| default_routing_table_name | OPTIONAL - Name of the Default Routing Table. If null, a name will be automatically generated | string |
null |
no |
| default_security_group_name | OPTIONAL - Name of the Default Security Group. If null, a name will be automatically generated | string |
null |
no |
| dns_binding_name | The name to give the provisioned VPC DNS resolution binding. If not set, the module generates a name based on the prefix and name variables. |
string |
null |
no |
| dns_custom_resolver_name | The name to give the provisioned DNS custom resolver instance. If not set, the module generates a name based on the prefix and name variables. |
string |
null |
no |
| dns_instance_name | The name to give the provisioned DNS instance. If not set, the module generates a name based on the prefix and name variables. |
string |
null |
no |
| dns_location | The target location or environment for the DNS instance created to host the custom resolver in a hub-spoke DNS resolution topology. Only used if enable_hub is true and skip_custom_resolver_hub_creation is false (defaults). | string |
"global" |
no |
| dns_plan | The plan for the DNS resource instance created to host the custom resolver in a hub-spoke DNS resolution topology. Only used if enable_hub is true and skip_custom_resolver_hub_creation is false (defaults). | string |
"standard-dns" |
no |
| enable_hub | Indicates whether this VPC is enabled as a DNS name resolution hub. | bool |
false |
no |
| enable_hub_vpc_crn | Indicates whether Hub VPC CRN is passed. | bool |
false |
no |
| enable_hub_vpc_id | Indicates whether Hub VPC ID is passed. | bool |
false |
no |
| enable_vpc_flow_logs | Flag to enable vpc flow logs. If true, flow log collector will be created | bool |
false |
no |
| existing_cos_instance_guid | GUID of the COS instance to create Flow log collector | string |
null |
no |
| existing_dns_instance_id | Id of an existing dns instance in which the custom resolver is created. Only relevant if enable_hub is set to true. | string |
null |
no |
| existing_storage_bucket_name | Name of the COS bucket to collect VPC flow logs | string |
null |
no |
| existing_subnets | The detail of the existing subnets and required mappings to other resources. Required if 'create_subnets' is false. | list(object({ |
[] |
no |
| existing_vpc_id | The ID of the existing vpc. Required if 'create_vpc' is false. | string |
null |
no |
| hub_account_id | ID of the hub account for DNS resolution, required if 'skip_spoke_auth_policy' is false. | string |
null |
no |
| hub_vpc_crn | Indicates the crn of the hub VPC for DNS resolution. See https://cloud.ibm.com/docs/vpc?topic=vpc-hub-spoke-model. Mutually exclusive with hub_vpc_id. | string |
null |
no |
| hub_vpc_id | Indicates the id of the hub VPC for DNS resolution. See https://cloud.ibm.com/docs/vpc?topic=vpc-hub-spoke-model. Mutually exclusive with hub_vpc_crn. | string |
null |
no |
| is_flow_log_collector_active | Indicates whether the collector is active. If false, this collector is created in inactive mode. | bool |
true |
no |
| manual_servers | The DNS server addresses to use for the VPC, replacing any existing servers. All the entries must either have a unique zone_affinity, or not have a zone_affinity. | list(object({ |
[] |
no |
| name | Used for the naming of the VPC (if create_vpc is set to true), as well as in the naming for any resources created inside the VPC (unless using one of the optional variables for explicit control over naming). | string |
n/a | yes |
| network_acls | The list of ACLs to create. Provide at least one rule for each ACL. | list( |
[ |
no |
| network_cidrs | List of Network CIDRs for the VPC. This is used to manage network ACL rules for cluster provisioning. | list(string) |
[ |
no |
| prefix | The value that you would like to prefix to the name of the resources provisioned by this module. Explicitly set to null if you do not wish to use a prefix. This value is ignored if using one of the optional variables for explicit control over naming. | string |
null |
no |
| public_gateway_name | The name to give the provisioned VPC public gateways. If not set, the module generates a name based on the prefix and name variables. |
string |
null |
no |
| region | The region to which to deploy the VPC | string |
n/a | yes |
| resolver_type | Resolver type. Can be system or manual. For delegated resolver type, see the update_delegated_resolver variable instead. | string |
null |
no |
| resource_group_id | The resource group ID where the VPC to be created | string |
n/a | yes |
| routes | OPTIONAL - Allows you to specify the next hop for packets based on their destination address | list( |
[] |
no |
| routing_table_name | The name to give the provisioned routing tables. If not set, the module generates a name based on the prefix and name variables. |
string |
null |
no |
| security_group_rules | A list of security group rules to be added to the default vpc security group (default empty) | list( |
[] |
no |
| skip_custom_resolver_hub_creation | Indicates whether to skip the configuration of a custom resolver in the hub VPC. Only relevant if enable_hub is set to true. | bool |
false |
no |
| skip_spoke_auth_policy | Set to true to skip the creation of an authorization policy between the DNS resolution spoke and hub, only enable this if a policy already exists between these two VPCs. See https://cloud.ibm.com/docs/vpc?topic=vpc-vpe-dns-sharing-s2s-auth&interface=ui for more details. | bool |
false |
no |
| subnets | List of subnets for the vpc. For each item in each array, a subnet will be created. Items can be either CIDR blocks or total ipv4 addressess. Public gateways will be enabled only in zones where a gateway has been created | object({ |
{ |
no |
| tags | List of Tags for the resource created | list(string) |
null |
no |
| update_delegated_resolver | If set to true, and if the vpc is configured to be a spoke for DNS resolution (enable_hub_vpc_crn or enable_hub_vpc_id set), then the spoke VPC resolver will be updated to a delegated resolver. | bool |
false |
no |
| use_existing_dns_instance | Whether to use an existing dns instance. If true, existing_dns_instance_id must be set. | bool |
false |
no |
| use_public_gateways | Create a public gateway in any of the three zones with true. |
object({ |
{ |
no |
| vpc_flow_logs_name | The name to give the provisioned VPC flow logs. If not set, the module generates a name based on the prefix and name variables. |
string |
null |
no |
| Name | Description |
|---|---|
| cidr_blocks | List of CIDR blocks present in VPC stack |
| custom_resolver_hub | The custom resolver created for the hub vpc. Only set if enable_hub is set and skip_custom_resolver_hub_creation is false. |
| dns_custom_resolver_id | The ID of the DNS Custom Resolver. |
| dns_endpoint_gateways_by_crn | The list of VPEs that are made available for DNS resolution in the created VPC. Only set if enable_hub is false and enable_hub_vpc_id are true. |
| dns_endpoint_gateways_by_id | The list of VPEs that are made available for DNS resolution in the created VPC. Only set if enable_hub is false and enable_hub_vpc_id are true. |
| dns_instance_id | The ID of the DNS instance. |
| network_acls | List of shortnames and IDs of network ACLs |
| public_gateways | Map of public gateways by zone |
| subnet_detail_list | A list of subnets containing names, CIDR blocks, and zones. |
| subnet_detail_map | A map of subnets containing IDs, CIDR blocks, and zones |
| subnet_ids | The IDs of the subnets |
| subnet_zone_list | A list containing subnet IDs and subnet zones |
| vpc_crn | CRN of VPC created |
| vpc_data | Data of the VPC used in this module, created or existing. |
| vpc_flow_logs | Details of VPC flow logs collector |
| vpc_id | ID of VPC created |
| vpc_name | Name of VPC created |
You can report issues and request features for this module in GitHub issues in the module repo. See Report an issue or request a feature.
To set up your local development environment, see Local development setup in the project documentation.

-brightgreen?style=plastic)